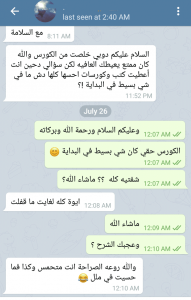
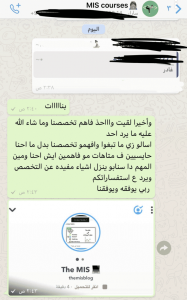
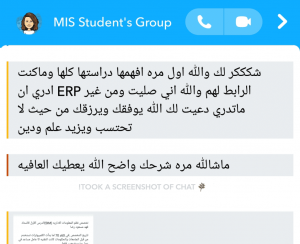
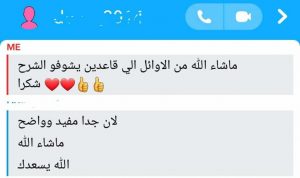
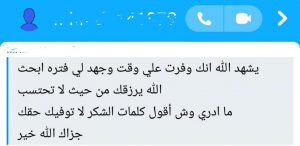
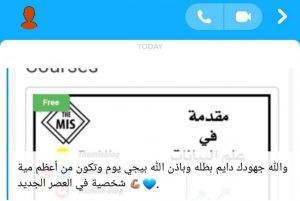
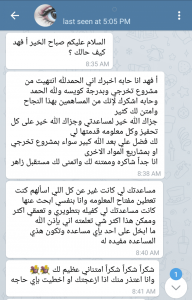
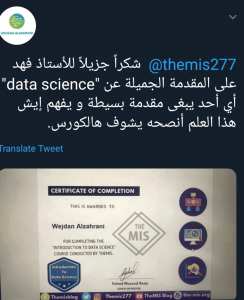
ستجد مقالات ودورات في المجالات التالية
سبب إنشاء الموقع

المدونة
Why MIS Graduates are facing difficulties in getting jobs !
،السادة الطلاب والخريجين الأعزاء يرجى قراءة الورقة البحثية التالية التي ستخبرك بنوع المهارات والمعرفة التي يجب أن تعرفها قبل التخرج...
Read MoreWhat is Management Information Systems (MIS)?
Management Information Systems (MIS) is the study of three major factors People Technology Organizations How do you study these factors...
Read MoreMIS or CIS?
This is probably the most confusing dichotomy that high school students face when they are deciding what career path to...
Read More
من أنا
أ/فهد مسعود رضا هو مدرس في مجال علم البيانات ومرشد نظم المعلومات الإدارية
ساعد العديد من الطلاب في فهم مفاهيم علم البيانات منذ عام 2016 ، وتوجيه مئات الطلاب في مجال نظم المعلومات الإدارية عبر موقعه الإلكتروني وقنوات التواصل الاجتماعي ، وهو حاصل على درجة البكالوريوس في مجال نظم المعلومات الإدارية ودرجة الماجستير في نظم المعلومات الحاسوبية (رسالة ماجستير في مجال علم البيانات) ، و ووردبريس ماستر لأكثر من 8 سنوات ويعمل حاليًا كمستشار في مجال الأعمال التجارية عبر الإنترنت والتعليم عبر الإنترنت.
تابعنا
تابعنا على مواقع التواصل الاجتماعي لتصلك خصومات عن الدورات والخدمات التي نقدمها