In recent days I’ve spotted many new hires from computer science asking me; what should I know about this field? What are the expected interview questions? For that, since everyone wants to know everything about information security. As an information security analyst myself I will include all career basics and I will include advantage topics in the future as a series.
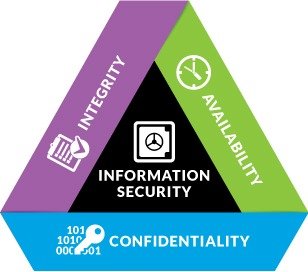
Information Security Analyst aka (ISA) is a field of planning and implementing security measures to an organization’s valuable assets wither its employees, systems, computer, network or buildings. These measures are referred to as (CIA) Confidentiality, Integrity, and Availability. In Confidentiality you want to take actions to protect the information secrecy and ensure that organizations’ valuable information is only readable by authorized personnel, example of a used tool > encryption. For Integrity, you are insuring that editing the data is done only by allowed employees and any unauthorized changes are detected and prevented. For example, of a used tool > hashes. Finally, Availability. In this matter, information must be available whenever its needed so DDOS attack (refer to as Distributed Deny of service attacks) are not blocking your employees from entering a necessary data. For example, of a used tool > backup, mirroring, RAID, cloud computing, etc.
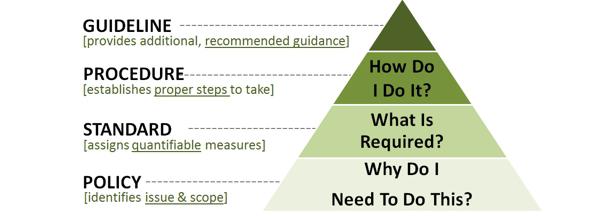
To implement security a policy must be raised and approved, and guidelines should be set in place to ensure everyone is following the steps to secure the company from breaches. You cannot enforce a policy without awareness about its benefits and how it is helping the organization. Awareness can include tips on how to secure your data for example, through backup and retention…etc.
Many companies are initiating their own information security program their names. They might be different from each other’s, but their goal is the same; securing information. These programs can include Risk Management, Information Asset Management, Physical Security Management, Awareness Program, Access Management, Backup and Retention Management, Business Continuity, Disaster Recover Management and External Party Management. Each one of these has a ton of tools and programs to manage them. On a monthly basis I will include details on how to achieve the goals of each programs’ elements until it is fully covered.
Referring to (http://www.cyberdegrees.org/jobs/security-analyst/) it is mentioned that you can build hard skills in :
- IDS/IPS, penetration and vulnerability testing
- DLP, anti-virus and anti-malware
- TCP/IP, computer networking, routing and switching
- Firewall and intrusion detection/prevention protocols
- Windows, UNIX and Linux operating systems
- Network protocols and packet analysis tools
- C, C++, C#, Java or PHP programming languages
- Cloud computing
- SaaS models
- Security Information and Event Management (SIEM)
These skills are not a must, but it is very useful to build throughout your career if you want to get good knowledge.

Do you have any courses
Until Now I have only one course , https://the-mis.org/arabic/courses/ , and there is a webinar I did a 2 weeks ago on my channel you can check it out from the following link: https://youtu.be/N2gkst912lM
Stay tuned for more courses , make sure to follow me on snap : themisblog for all the updates
Wish you all the best
Fahad